Jaff Ransomware Distributed via Necurs MALSPAM and asking for a $3,700 Ransom
A new ransomware was found today by Malwarebytes' malware researcher S!Ri called Jaff Ransomware. In general, there is nothing special about this ransomware other than it is being heavily distributed and that they stole the payment site html from Locky. Otherwise, Jaff is your garden variety ransomware that encrypts files using AES encryption and appends the .jaff extension to encrypted files.
Unfortunately, after analysis by Emsisoft's Fabian Wosar it was determined that the Jaff Ransomware is not decryptable. With that said, there may be methods that can be used to recover some of the files, so please contact Emsisoft or the helpers at BleepingComputer before paying a ransom. If you want to discuss this ransomware or receive support, you can ask in our dedicated Jaff Ransomware Support & Help Topic.
Now, let's take a look at how Jaff is being distributed and executed.
Jaff Ransomware being Distributed by MALSPAM
According to CERT-Bund, Jaff is being heavily distributed via MALSPAM from the Necurs botnet. These SPAM emails will have subjects like Scan_84686473 and will contain an attached PDF called nm.pdf. The different subject lines that are being used are:
Copy_[Random Numbers]
Document_[Random Numbers]
Scan_[Random Numbers]
File_[Random Numbers]
PDF_[Random Numbers]
When a victim opens the SPAM email all they will see is the PDF attachment as shown below.
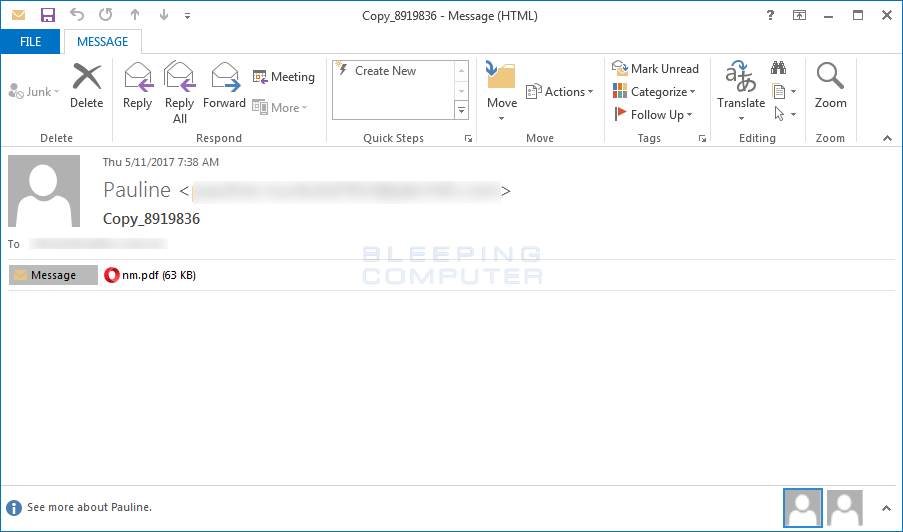
Depending on the PDF reader, when the user opens the PDF they will either be prompted to open an embedded DOCM file or it will be launched immediately.
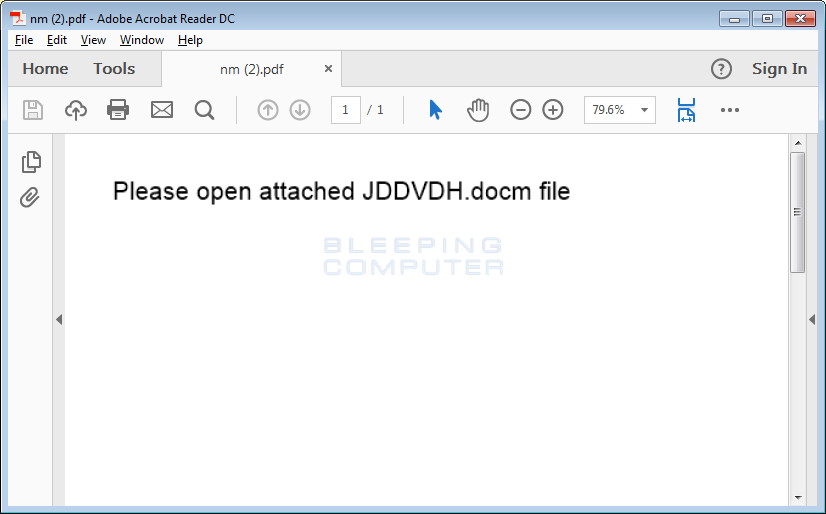
Once the DOCM is launched, the victim will be greeted with the typical message that they must Enable Content to properly read the document.
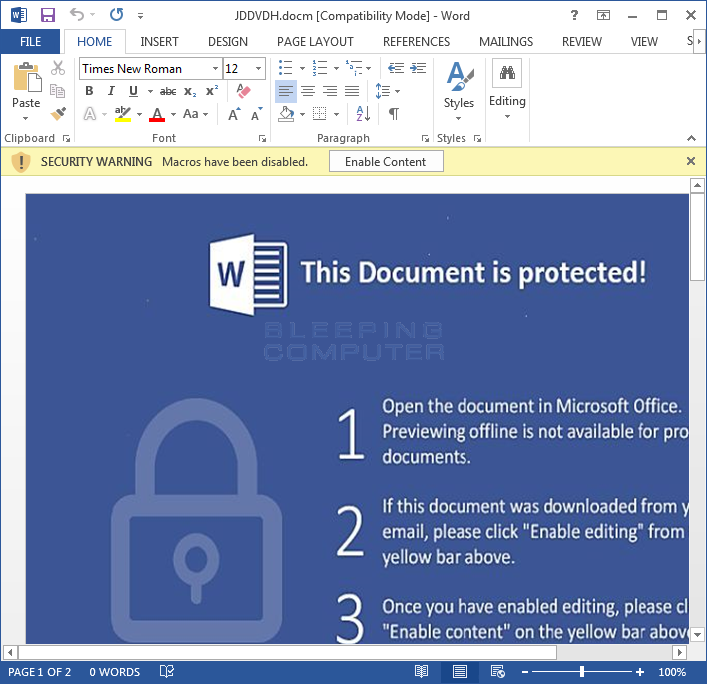
Unfortunately, once they enable the content, and thus enable macros, the macros will fire off and gather information about the users on the computer and download and execute various files on the machine. You can see an image of the various macros embedded in this document below.
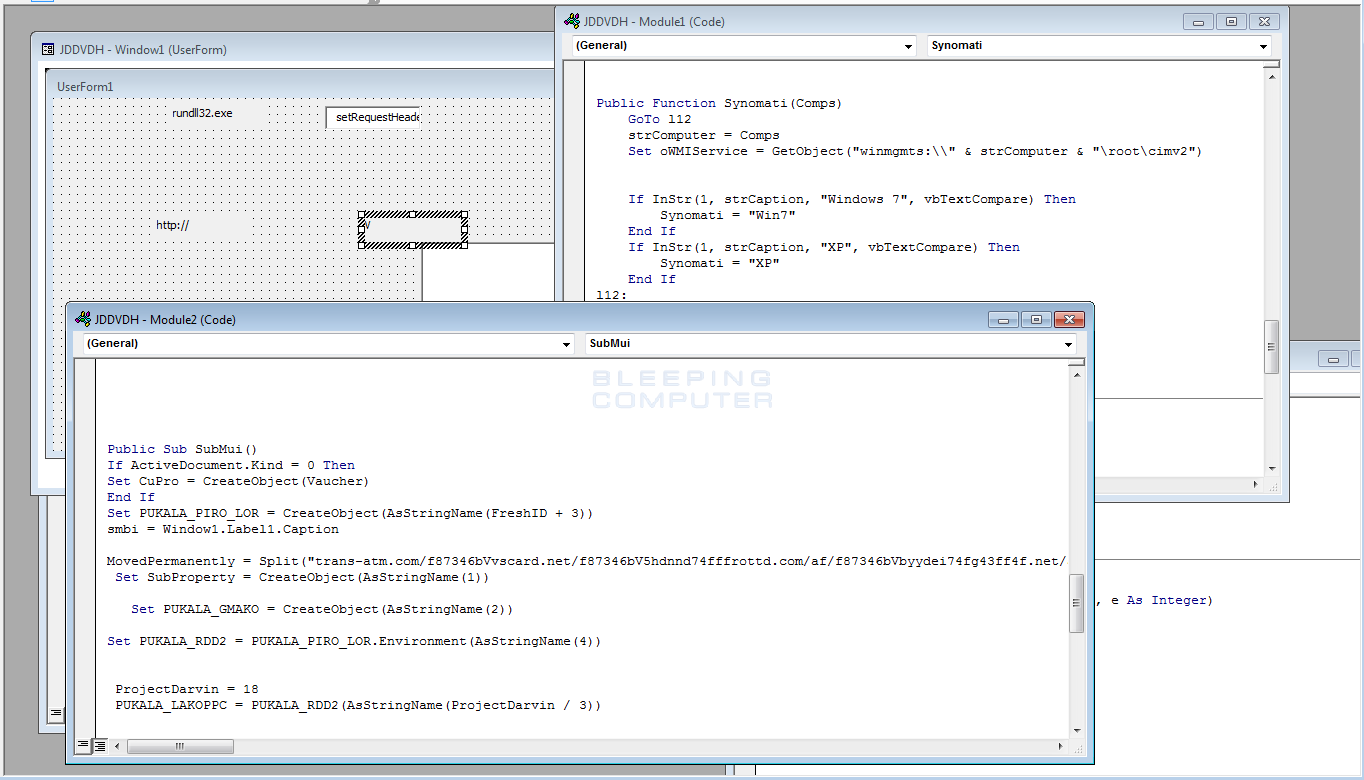
In the above image, the macro titled JDDVDH has a MovedPermanently string in it. This string is a series of URLs that the macro will use to download and execute files to the machine. At the time of this writing, only 1 out of the 3 URLs were still working.
Once the Jaff Ransomware executable is downloaded, it will be automatically executed and begin the encryption of the vicitm's computer. More details about this process are in the next section.
How the Jaff Ransomware Encrypts a Computer
When the Jaff installer is downloaded and executed, the program will connect to a Command & Control, or C2, server located at http://fkksjobnn43.org/a5/ in order to indicate that a new victim is being encrypted. The Command & Control server will then respond with the single word "Created". No other information is transmitted between the C2 server and the infected victim from this point forward.
Jaff will now begin to encrypt the victims computer using AES encryption. When encrypting a computer, Jaff will only encrypt files that contain certain file extensions. The file extensions targeted by Jaff are:
xlsx .acd .pdf .pfx .crt .der .cad .dwg .MPEG .rar .veg .zip .txt .jpg .doc .wbk .mdb .vcf .docx .ics .vsc .mdf .dsr .mdi .msg .xls .ppt .pps .obd .mpd .dot .xlt .pot .obt .htm .html .mix .pub .vsd .png .ico .rtf .odt .3dm .3ds .dxf .max .obj .7z .cbr .deb .gz .rpm .sitx .tar .tar.gz .zipx .aif .iff .m3u .m4a .mid .key .vib .stl .psd .ova .xmod .wda .prn .zpf .swm .xml .xlsm .par .tib .waw .001 .002 003. .004 .005 .006 .007 .008 .009 .010 .contact .dbx .jnt .mapimail .oab .ods .ppsm .pptm .prf .pst .wab .1cd .3g2 .7ZIP .accdb .aoi .asf .asp. aspx .asx .avi .bak .cer .cfg .class .config .css .csv .db .dds .fif .flv .idx .js .kwm .laccdb .idf .lit .mbx .md .mlb .mov .mp3 .mp4 .mpg .pages .php .pwm .rm .safe .sav .save .sql .srt .swf .thm .vob .wav .wma .wmv .xlsb .aac .ai .arw .c .cdr .cls .cpi .cpp .cs .db3 .docm .dotm .dotx .drw .dxb .eps .fla .flac .fxg .java .m .m4v .pcd .pct .pl .potm .potx .ppam .ppsx .ps .pspimage .r3d .rw2 .sldm .sldx .svg .tga .wps .xla .xlam .xlm .xltm .xltx .xlw .act .adp .al .bkp .blend .cdf .cdx .cgm .cr2 .dac .dbf .dcr .ddd .design .dtd .fdb .fff .fpx .h .iif .indd .jpeg .mos .nd .nsd .nsf .nsg .nsh .odc .odp .oil .pas .pat .pef .ptx .qbb .qbm .sas7bdat .say .st4 .st6 .stc .sxc .sxw .tlg .wad .xlk .aiff .bin .bmp .cmt .dat .dit .edb .flvv .gif .groups .hdd .hpp .log .m2ts .m4p .mkv .ndf .nvram .ogg .ost .pab .pdb .pif .qed .qcow .qcow2 .rvt .st7 .stm .vbox .vdi .vhd .vhdx .vmdk .vmsd .vmx .vmxf .3fr .3pr .ab4 .accde .accdt .ach .acr .adb .srw .st5 .st8 .std .sti .stw .stx .sxd .sxg .sxi .sxm .tex .wallet .wb2 .wpd .x11 .x3f .xis .ycbcra .qbw .qbx .qby .raf .rat .raw .rdb rwl .rwz .s3db .sd0 .sda .sdf .sqlite .sqlite3 .sqlitedb .sr .srf .oth .otp .ots .ott .p12 .p7b .p7c .pdd .pem .plus_muhd .plc .pptx .psafe3 .py .qba .qbr.myd .ndd .nef .nk .nop .nrw .ns2 .ns3 .ns4 .nwb .nx2 .nxl .nyf .odb .odf .odg .odm .ord .otg .ibz .iiq .incpas .jpe .kc2 .kdbx .kdc .kpdx .lua .mdc .mef .mfw .mmw .mny .moneywell .mrw.des .dgc .djvu .dng .drf .dxg .eml .erbsql .erd .exf .ffd .fh .fhd .gray .grey .gry .hbk .ibank .ibd .cdr4 .cdr5 .cdr6 .cdrw .ce1 .ce2 .cib .craw .crw .csh .csl .db_journal .dc2 .dcs .ddoc .ddrw .ads .agdl .ait .apj .asm .awg .back .backup .backupdb .bank .bay .bdb .bgt .bik .bpw .cdr3 .as4
After encrypting a file, Jaff will encrypt the AES encryption key with a bundled RSA key and append it to the beginning of the encrypted file. You can see an example of this in the image below, which shows an encrypted file in a hex editor.
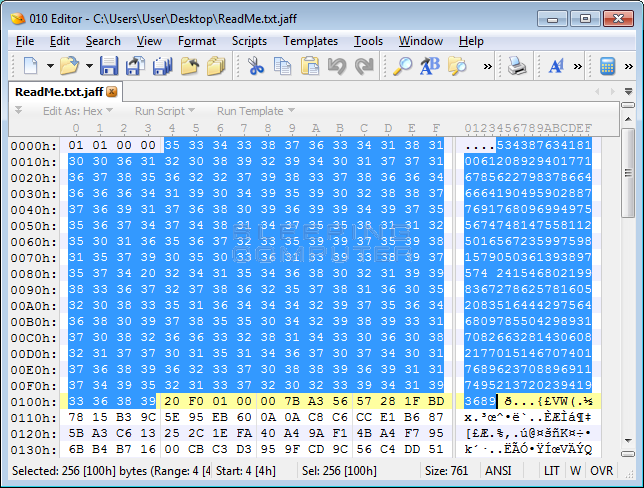
The ransomware will then append the .jaff extension to the newly encrypted file to denote that it has been encrypted. For example, a file named test.jpg would now be encrypted as test.jpg.jaff.
The ransomware will also store a BMP file called WallpapeR.bmp in the C:\ProgramData\Rondo folder that is used as the desktop wallpaper. Finally, while encrypting files, it will create ransom notes throughout the hard drive named ReadMe.bmp, ReadMe.html, and ReadMe.txt. These ransom notes contain a unique 10 digit "decrypt ID" and the address to a TOR site where a victim can make payment.
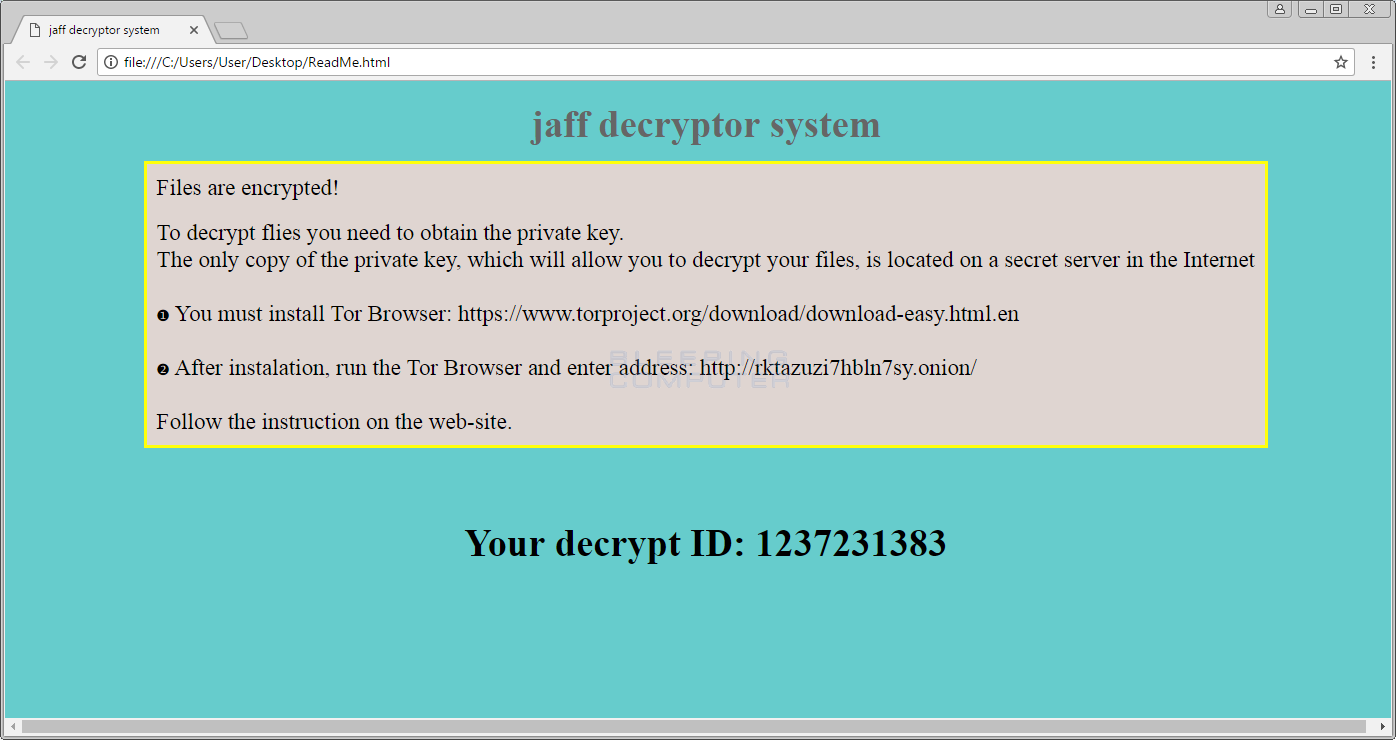
When a victim goes to the TOR site they will be prompted to enter their ID and will then be greeted by a site titled "jaff decryptor system" as shown below. This site contains information on how to pay the ransom, the bitcoin ransom amount, and the bitcoin address payments must be sent to. Currently, the bitcoin ransom payments are around 2 bitcoins, which equates to ~3,700 USD.
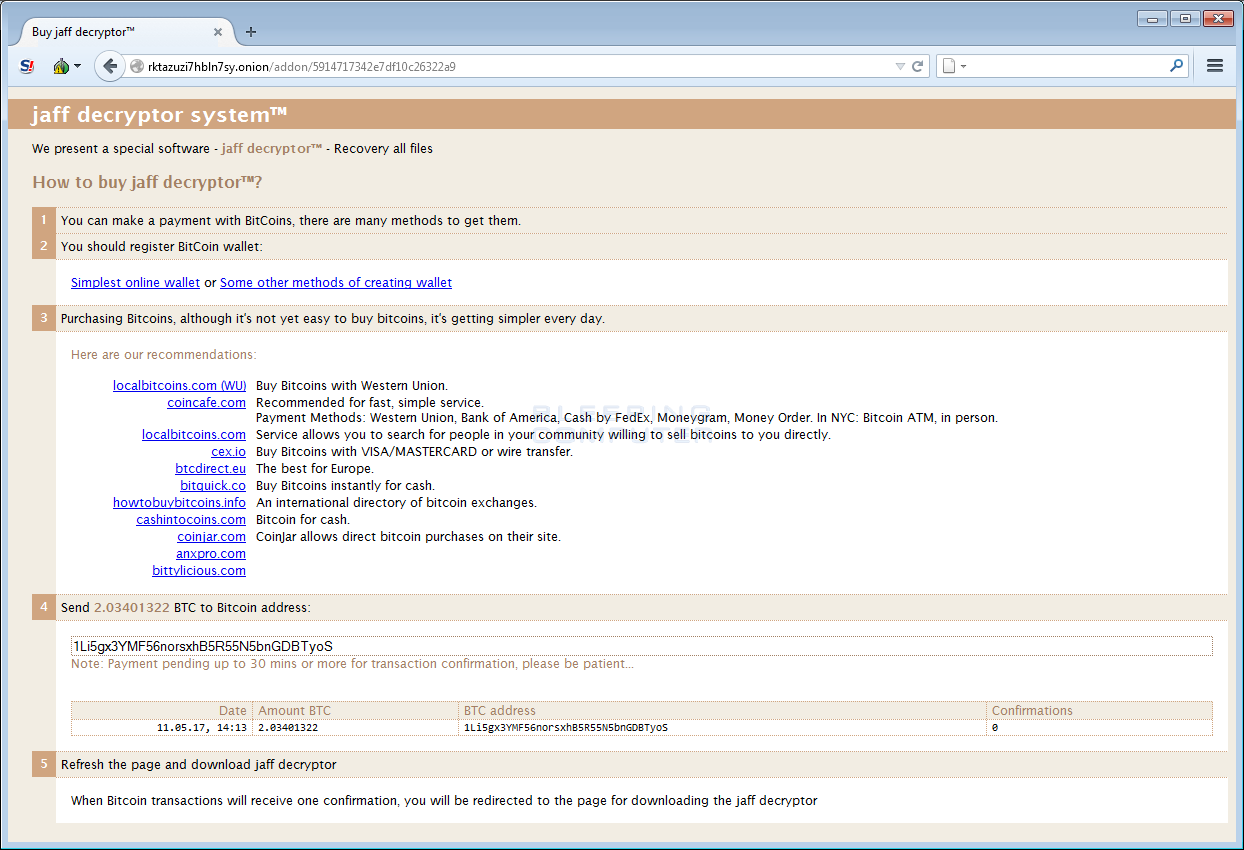
For those who are familiar with ransomware, this payment screen may look familiar to you. This is because the Jaff Ransomware developers stole the layout and html used by Locky. This does not mean, though, Jaff is a variant of Locky as the complexity and functionality of Jaff is very different than Locky. The general consensus is that this is a completely new family that simply stole Locky's payment site HTML.
As previously stated. unfortunately the Jaff Ransomware is not decryptable for free. With that said, there may be ways to get your files back without making a payment, so please be sure to contact us or Emsisoft for help. You can ask for help in our dedicated Jaff Ransomware Help & Support Topic.
How can you Protect Yourself from Ransomware?
If you were infected by Jaff, I can only say that I know what you are going through is terrible. I have helped enough people with ransomware over the past 5 years to know that its a horrible and violating experience and not one I wish on anyone.
For anyone who was infected with the Jaff Ransomware or is concerned about future infections, I highly recommend Emsisoft Anti-Malware for their behavior blocker component. Not only do you get a great security program, but their behavior blocker has an incredible track record at preventing new zero-day ransomware from encrypting a computer.
This is what happened when I tried running the Jaff installer with Emsisoft Anti-Malware's Behavior Blocker enabled.
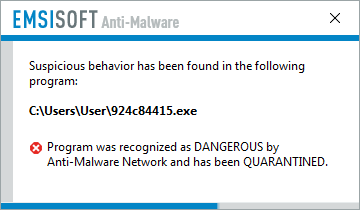
Unfortunately, the behavior blocker is only available in the paid for version, so you would need to purchase Emsisoft Anti-malware in order to benefit from this feature.
In full disclosure, we do earn a commission if you purchase Emsisoft Anti-Malware through the above link. With that said, I am only recommending Emsisoft Anti-malware because I believe in the program and that it can do a terrific job protecting you from Ransomware and other malware.
IOCs
Jaff Ransomware Hashes:
SHA256: 0746594fc3e49975d3d94bac8e80c0cdaa96d90ede3b271e6f372f55b20bac2fFiles Associated with the Jaff Ransomware:
C:\ProgramData\Rondo\
C:\ProgramData\Rondo\backup.om\
C:\ProgramData\Rondo\WallpapeR.bmp\
ReadMe.bmp
ReadMe.html
ReadMe.txtRegistry Entries Associated with the Jaff Ransomware:
HKCU\Control Panel\Desktop\Wallpaper "C:\ProgramData\Rondo\WallpapeR.bmp"
Network Communication Associated with the Jaff Ransomware:
http://rktazuzi7hbln7sy.onion/
http://fkksjobnn43.org/a5/
Jaff Ransomware Note:
jaff decryptor system
Files are encrypted!
To decrypt flies you need to obtain the private key.
The only copy of the private key, which will allow you to decrypt your files, is located on a secret server in the Internet
? You must install Tor Browser: https://www.torproject.org/download/download-easy.html.en
? After instalation, run the Tor Browser and enter address: http://rktazuzi7hbln7sy.onion/
Follow the instruction on the web-site.
Your decrypt ID: 1237231383



Post a Comment