CSAPP - Buffer Overflow Attacks / Bufbomb Lab
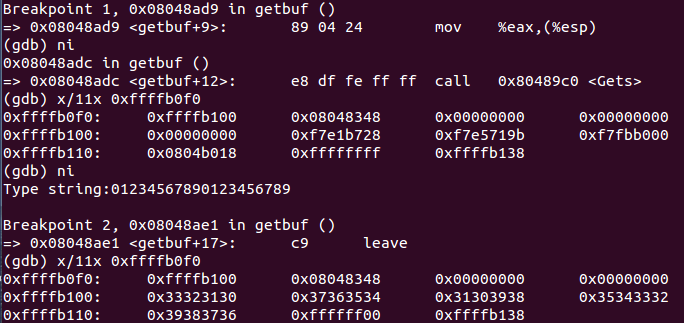
This assignment will help you develop a detailed understanding of IA-32 calling conventions and stack organization. It involves applying a series of buffer overflow attacks on an executable file bufbomb in the lab directory.
Assignment
- Computer Systems, Spring 2017
- Lab Assignment 3: The Buffer Bomb
- Assigned: Apr. 20
- Computer Systems, Spring 2017
- Lab Assignment 3: The Buffer Bomb
- Assigned: Apr. 20
Note:
In this lab, you will gain firsthand experience with one of the methods commonly used to exploit security weaknesses in operating systems and network servers. Our purpose is to help you learn about the runtime operation of programs and to understand the nature of this form of security weakness so that you can avoid it when you write system code. We do not condone the use of this or any other form of attack to gain unauthorized access to any system resources. There are criminal statutes governing such activities.
In this lab, you will gain firsthand experience with one of the methods commonly used to exploit security weaknesses in operating systems and network servers. Our purpose is to help you learn about the runtime operation of programs and to understand the nature of this form of security weakness so that you can avoid it when you write system code. We do not condone the use of this or any other form of attack to gain unauthorized access to any system resources. There are criminal statutes governing such activities.
Three executable files:
+ bufbomb: The buffer bomb program you will attack.
+ makecookie: Generates a “cookie” based on your userid.
+ hex2raw: A utility to help convert between string formats.
+ bufbomb: The buffer bomb program you will attack.
+ makecookie: Generates a “cookie” based on your userid.
+ hex2raw: A utility to help convert between string formats.
Please read buflab.pdf Before run those program!
git clone https://github.com/zhwhong/Bufbomb_CSAPP && cd Bufbomb_CSAPP
Example:
./makecookie seclist
./bufbomb -u seclist



Post a Comment