Sniffing GSM traffic with HackRF
GOOD LUCK!
Tools used:
Install Requirements:
First thing, you want to make sure you have all the required software installed, you can install most of them and their dependencies using your distribution package manager. Let’s start with the libraries and tools for the hackrf itself, on a Debian/Ubuntu distro you’ll install them like so:
1
| sudo apt-get install hackrf libhackrf-dev libhackrf0 |
Once these libraries are installed, you can plug your hackrf into one of your USB ports and execute the hackrf_info command, at this point you should see something like the following:
1
2
3
4
5
6
7
| # hackrf_infoFound HackRF board.Board ID Number: 2 (HackRF One)Firmware Version: 2014.08.1Part ID Number: 0x00574746 0x00574746Serial Number: 0x00000000 0x00000000 0x14d463dc 0x2f4339e1 |
You will now install gnuradio which is the software we’ll use to decode the RF signals, gqrx a tool to visualize signal power on certain frequencies and everything else that will be needed in the next steps:
1
| sudo apt-get install gnuradio gnuradio-dev gr-osmosdr gr-osmosdr gqrx-sdr wireshark |
Proceed with gr-gsm, the GnuRadio blocks that will decode GSM packets:
1
2
3
4
5
6
7
8
9
| sudo apt-get install git cmake libboost-all-dev libcppunit-dev swig doxygen liblog4cpp5-dev python-scipygit clone https://github.com/ptrkrysik/gr-gsm.gitcd gr-gsmmkdir buildcd buildcmake ..makesudo make installsudo ldconfig |
Now create the file ~/.gnuradio/config.conf and paste the following contents into it:
1
2
| [grc]local_blocks_path=/usr/local/share/gnuradio/grc/blocks |
Finally install kalibrate-hackrf, a tool that will hop among known GSM frequencies and will tell you which your country is using:
1
2
3
4
5
6
| git clone https://github.com/scateu/kalibrate-hackrf.gitcd kalibrate-hackrf./bootstrap./configuremakesudo make install |
Finding GSM Frequencies:
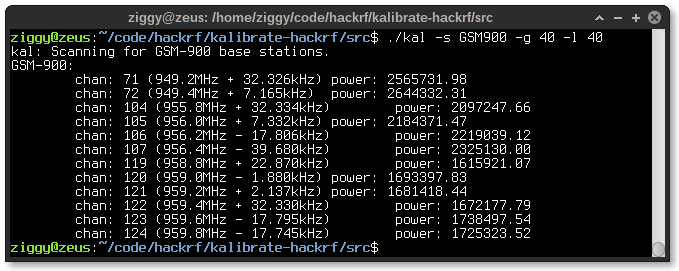
Each operator in each country uses a different frequency in the GSM possible spectrum, which usually starts from 900Mhz. You can use hackrf_kalibrate to find the frequencies you want to sniff:
1
| ./kal -s GSM900 -g 40 -l 40 |
Note the two gain values, those are important in order to get some results. Leave kalibrate running and after a while you should see an output similar to this:
You will have to use the proper GSM parameter (‘-s’) to correspond to your local operator. Consult this list for verification.
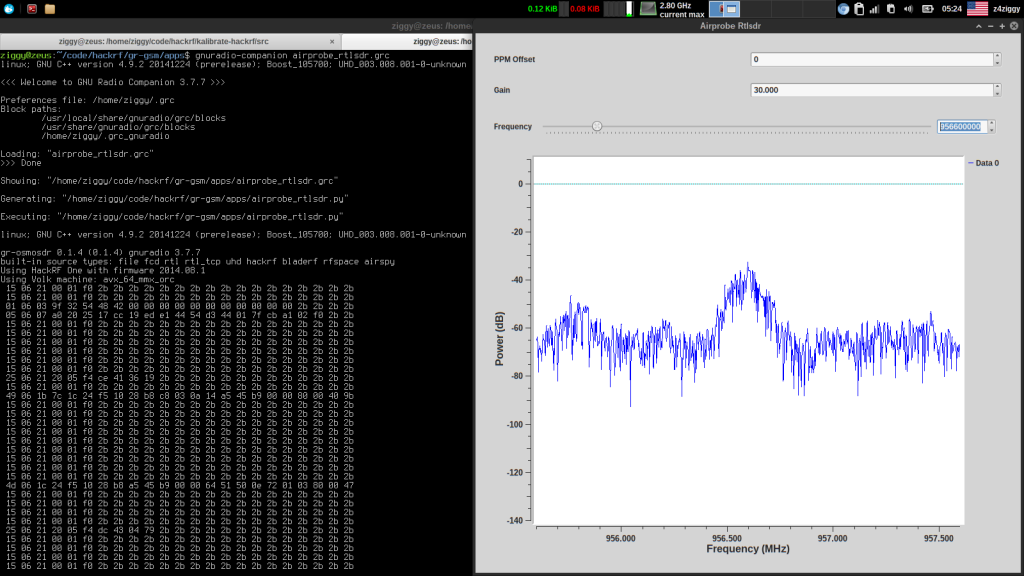
Sometimes you might want to see the frequencies in order to ensure correct results from hackrf_kalibrate, or to save yourself from calculating the correct frequency given by hackrf_kalibrate (notice the +/- Khz sign of each result – this means the top peak with the corresponding power,not 100% correct frequency). Open gqrx and tune it to the first frequency you got from hackrf_kalibrate, for example 940.6Mhz, and you’ll see something like the following picture:
In the above screenshot you can visually see the activity is around 945Mhz.
Once you know the GSM channels frequencies, you can start gr-gsm by running the python script ./airprobe_rtlsdr.py or load the airprobe_rtlsdr.grc file using gnuradio-companion and set one of the channel frequencies you just found in the frequency field. Don’t forget to add ‘gain’ value again, move back to the frequency field and start pressing the UP/DOWN arrows on your keyboard to start scrolling the frequencies in 200Khz steps until you start seeing some data in your console window. The whole process should look something like this:
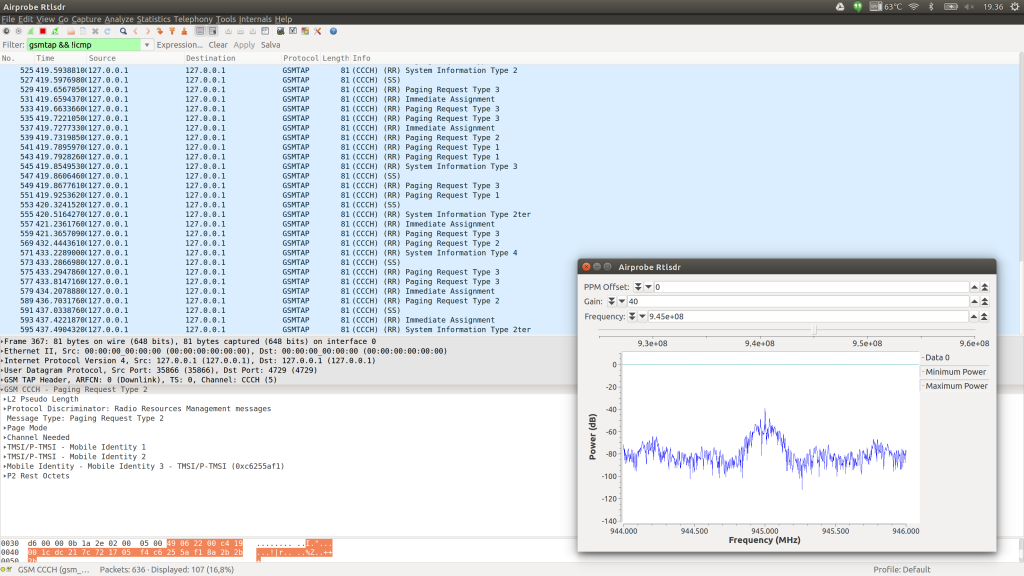
Now you only need to launch wireshark from another terminal tab with the following command:
1
| sudo wireshark -k -Y 'gsmtap && !icmp' -i lo |





Post a Comment