Cameradar - Hacks its way into RTSP CCTV cameras
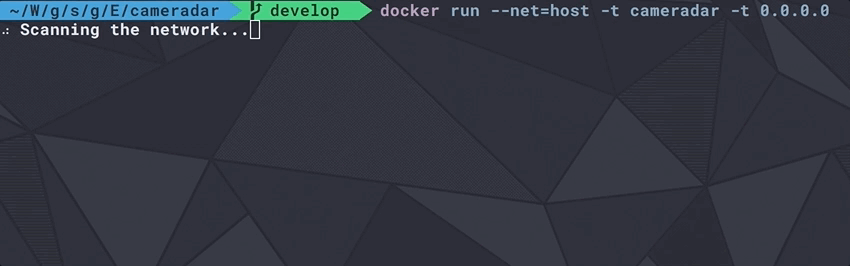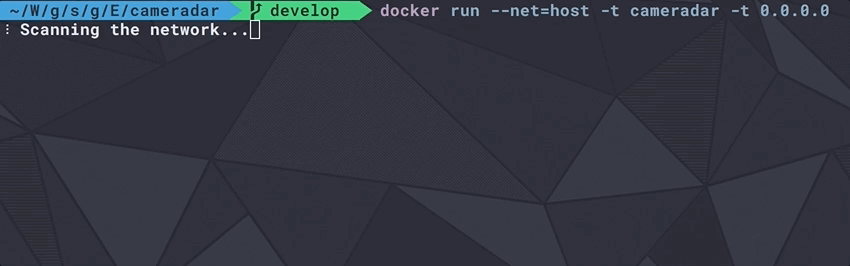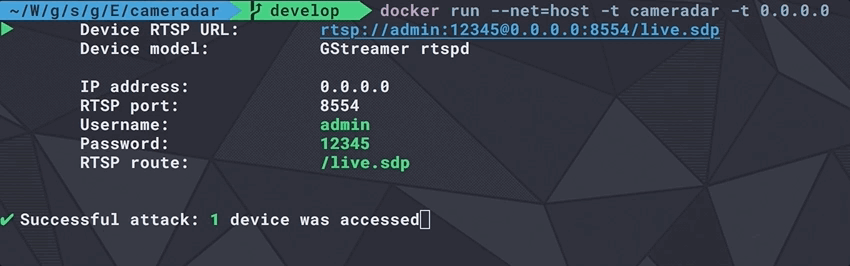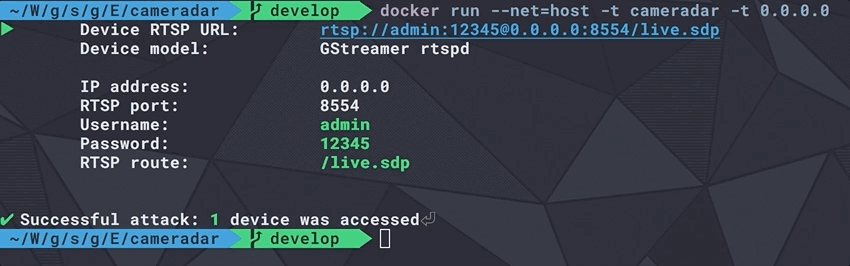
Cameradar allows you to
- Detect open RTSP hosts on any accessible target host
- Detect which device model is streaming
- Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp)
- Launch automated dictionary attacks to get the username and password of the cameras
- Retrieve a complete and user-friendly report of the results
Docker Image for Cameradar
Install docker on your machine, and run the following command:
e.g.: docker run -t ullaakut/cameradar -t 192.168.100.0/24 -l will scan the ports 554 and 8554 of hosts on the 192.168.100.0/24 subnetwork and attack the discovered RTSP streams and will output debug logs.
- YOUR_TARGET can be a subnet (e.g.: 172.16.100.0/24), an IP (e.g.: 172.16.100.10), or a range of IPs (e.g.: 172.16.100.10-20).
- If you want to get the precise results of the nmap scan in the form of an XML file, you can add -v /your/path:/tmp/cameradar_scan.xml to the docker run command, before ullaakut/cameradar.
- If you use the -r and -c options to specify your custom dictionaries, make sure to also use a volume to add them to the docker container. Example: docker run -t -v /path/to/dictionaries/:/tmp/ ullaakut/cameradar -r /tmp/myroutes -c /tmp/mycredentials.json -t mytarget
Installing the binary
Dependencies
- go
- glide
Installing glide
- OSX: brew install glide
- Linux: curl https://glide.sh/get | sh
- Windows: Download the binary package here
Steps to install
Make sure you installed the dependencies mentionned above.
- go get github.com/EtixLabs/cameradar
- cd $GOPATH/src/github.com/EtixLabs/cameradar
- glide install
- cd cameradar
- go install
The cameradar binary is now in your $GOPATH/bin ready to be used. See command line options here.
Library
Dependencies of the library
- curl-dev / libcurl (depending on your OS)
- nmap
- github.com/pkg/errors
- gopkg.in/go-playground/validator.v9
- github.com/andelf/go-curl
Installing the library
go get github.com/EtixLabs/cameradar
After this command, the cameradar library is ready to use. Its source will be in:
$GOPATH/src/pkg/github.com/EtixLabs/cameradar
You can use go get -u to update the package.
Here is an overview of the exposed functions of this library:
Discovery
You can use the cameradar library for simple discovery purposes if you don't need to access the cameras but just to be aware of their existence.
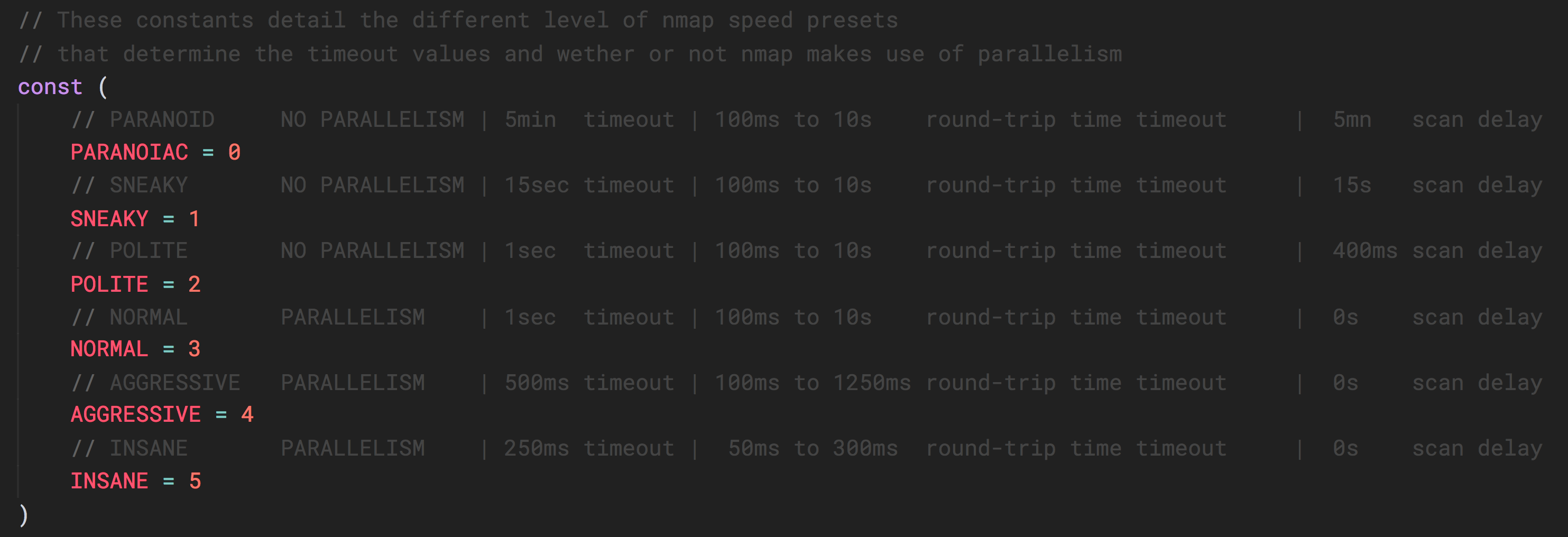
This describes the nmap time presets. You can pass a value between 1 and 5 as described in this table, to the NmapRun function.Attack
If you already know which hosts and ports you want to attack, you can also skip the discovery part and use directly the attack functions. The attack functions also take a timeout value as a parameter.
Data models
Here are the different data models useful to use the exposed functions of the cameradar library.
Dictionary loaders
The cameradar library also provides two functions that take file paths as inputs and return the appropriate data models filled.




Post a Comment